

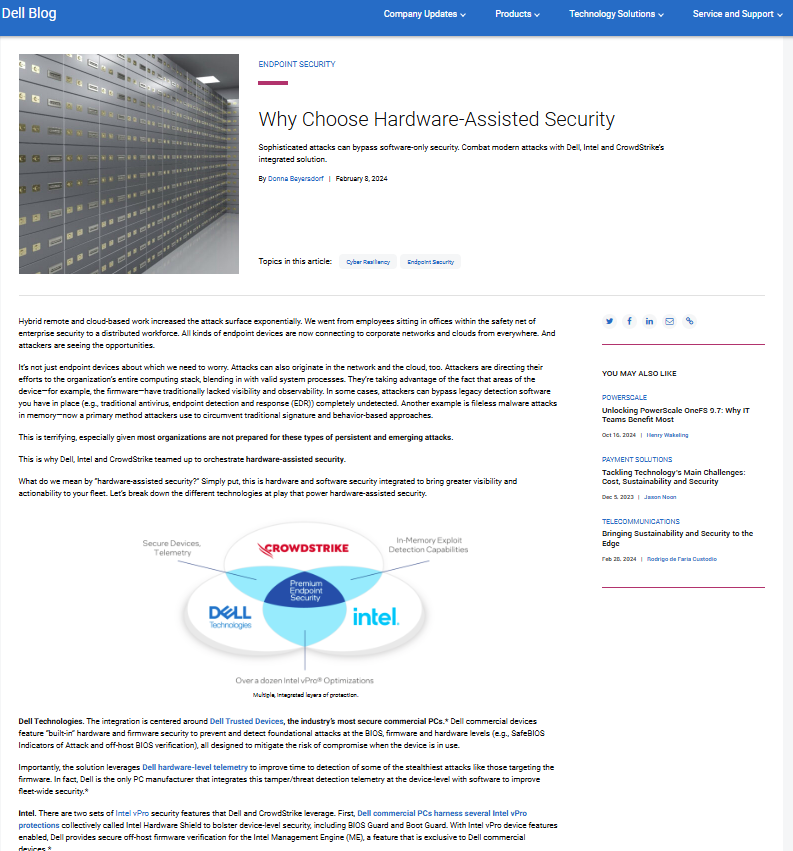
Hybrid remote and cloud-based work
increased the attack surface exponentially. We went from employees sitting in offices within
the safety net of enterprise security to a distributed workforce. All kinds of endpoint
devices are now connecting to corporate networks and clouds from everywhere. And attackers
are seeing the opportunities.
It’s not just endpoint devices about which we need
to worry. Attacks can also originate in the network and the cloud, too. Attackers are
directing their efforts to the organization’s entire computing stack, blending in with valid
system processes. They’re taking advantage of the fact that areas of the device—for example,
the firmware—have traditionally lacked visibility and observability. In some cases,
attackers can bypass legacy detection software you have in place (e.g., traditional
antivirus, endpoint detection and response (EDR)) completely undetected. Another example is
fileless malware attacks in memory—now a primary method attackers use to circumvent
traditional signature and behavior-based approaches.


Intel vPro® platform, Built for Business